
The mobile application ecosystem is a big, complicated place. You have all these incredible features like web support, plugins, and extensions. But with each new functionality come new security vulnerabilities, which—one way or another—hackers find a way to exploit. With this blog, I want to specifically talk about vulnerabilities in the iOS app ecosystem. Apple has a pretty solid track record with security on their devices and apps, and they boast extensive computing power and increasingly feature-rich & complex frameworks.That said, their prominence in the world of tech also makes them a particularly high-value target for attackers. Exploits like Information Gathering, Bypass Techniques, and Privacy Breaches are just a few in the long list of iOS attacks.One of the latest exploits to be featured in the news was the zero-click attack on a Bahraini human rights activists who was hacked with NSO's Pegasus spyware. It’s called ‘zero-click’ because it doesn’t require any user interaction to infect a victim’s device. If that sounds disconcerting, that’s because it is.The attack took advantage of a previously unknown security vulnerability in Apple’s iMessage app, which was exploited to push the Pegasus spyware, developed by Israeli firm NSO Group, to the activist’s phone.But while there’s no such thing as an ‘unhackable’ software, you can still make your application so hard to crack, hackers won’t even want to bother trying. Sure, it doesn’t roll off the tongue quite as nicely, but at least you’re being realistic.So here are the 4 steps you can take to make your iOS app bulletproof:
Design a Threat Model against various attack scenarios
Learn from the mistakes of various exploits and build a stronger fortification
Employ tools & methods that work to block these attacks for stronger applications
Implement best practices to create awareness and a secure ethos
Threat Modeling is like designing an application and the various scenarios built around it. It's an exercise that helps to identify potential risks and loopholes in the iOS application. You can learn more about we45's threat modeling services here. Threat modeling helps identify security concerns such as:
[caption id="attachment_6830" align="aligncenter" width="620"]

Sample Threat Model 1 : Authenticate the User and display Bank Balance[/caption]Mobile operating systems implement controls like sandboxing and permission enforcement to limit malicious application access
Web applications are accessible from iOS devices using mobile browsers. When accessing web apps in this manner, some controls and threat agents are different.[caption id="attachment_6832" align="aligncenter" width="690"]
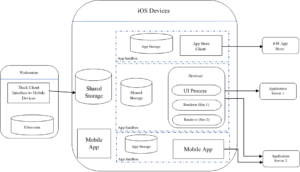
Securing an iOS app from various attacks[/caption]This table depicts how various threats are controlled through different surface attacks: Assets ControlsThreats Application Data Certification Verification Malicious App Users Application Functionality Cache Malicious Websites Cookies Browser Processes Physical access to Device DOM Objects User AuthN/AuthZMalicious Attackers User’s Private Data Application Permissions Device Functionality Same Origin Policy
This table represents a few of threat concerns and the mode of attack: Threat Agent Attack Surface Target Assets Controls Malicious app users BrowserUsers’ private data Device functionality Sandbox the browser and application Enforce app permissions Malicious app (sandboxed) App sandboxing Mobile device Application data Application functionality Cookies Users’ private data Device functionality Store verification Enforce app permissions. The controls listed reduce the likelihood of the malicious apps accessing the user’s private data stored on the device. Mobile operating systems like iOS implement controls like sandboxing and enforcing permissions to limit malicious application access. It’s important learn from your mistakes (or better yet, someone else’s)!
iOS jailbreaking is often compared to Android rooting, but the process is quite different. Here’s an explanation of how it works on Android. Rooting: This involves installing the binary on the system or replacing the whole system with a rooted custom ROM. Flashing custom ROMs: This allows you to replace the OS that's running on the device after you unlock the bootloader. The bootloader may require an exploit to unlock it But for on iOS devices, flashing a custom ROM is impossible because the iOS bootloader only allows Apple-signed images to be booted and flashed. This is why even official iOS images can't be installed if they aren't signed by Apple, and it makes iOS downgrades only possible for as long as the previous iOS version is still signed. This makes it more complicated because Apple keeps hardening the system and patching the exploited vulnerabilities.
Use SHA-2 or SHA-3 for hashing and AES for two-way encryption. Pick the best solution that provides your application with safety and security without any compromise.
When apps connect to a remote server, there are usually some short-lived access tokens generated to talk to the API’s. A good habit would be to store these tokens, using User Defaults, and reuse them before it expires. But this has a flip side too, since User Defaults stores as aplist file, totally readable. The solution is to store any data/file in an encrypted form, using Encrypted Shared Preferences.
There are numerous ways that an app can be exploited for its data, usage, user coverage, etc. As many apps exist, so do exploit tools. These can be used both for malicious purposes or for securing applications. Some of the most common attacks :
These are some of the best practices to implement over tools and bypass techniques to secure your application and safeguard the user’s data. However, not everything is feasible to implement, depending on business requirements and other constraints. Some of my favourite bypass/exploit tools: Objection (root detection), SSL Pinning bypass, Nmap, Openvas, Directory Listing, Nikto, subdomain find/enumeration, SSL Scan/Testssl/Qualys_SSL labs, CSP Evaluator/Security Headers, Burp suite- Spidering, OWASP ZAP, Active scans.
As strong as Apple can make its security measures, the surface attacks on their applications and devices are stronger. Almost every app stores some kind of data on the device. With integrated threat detection and alerting, we should work to close the loop between protecting iOS apps and understanding their real-time threat pressure. Protecting iOS applications is critical to managing risk in a zero-trust world.